Multi-Phase Security: A Comprehensive Framework for Decentralized Security
Explore how Particle CS's multi-phase security framework eliminates single points of failure in blockchain operations through staged approvals and time-delayed execution. Learn how to implement enterprise-grade security for digital assets.
Table of Contents
 Visual: Multi-phase security process flow showing the staged approval and execution workflow
Visual: Multi-phase security process flow showing the staged approval and execution workflow
The Challenge: Single Points of Failure in Blockchain Security
In today’s blockchain landscape, traditional security measures are falling short. The conventional approach of relying on a single private key for authorization has proven to be a critical vulnerability, leading to billions of dollars in losses through phishing, social engineering, and operational mistakes. But what if there was a better way?
The Multi-Phase Security Framework
The Multi-Phase Security Framework introduces multiple, independent security layers that must be satisfied before any operation can execute. This approach eliminates single points of failure by ensuring no single compromised key can execute a transaction. It provides recovery windows through time delays, enables role separation for different parties, and supports compliance requirements through built-in controls.
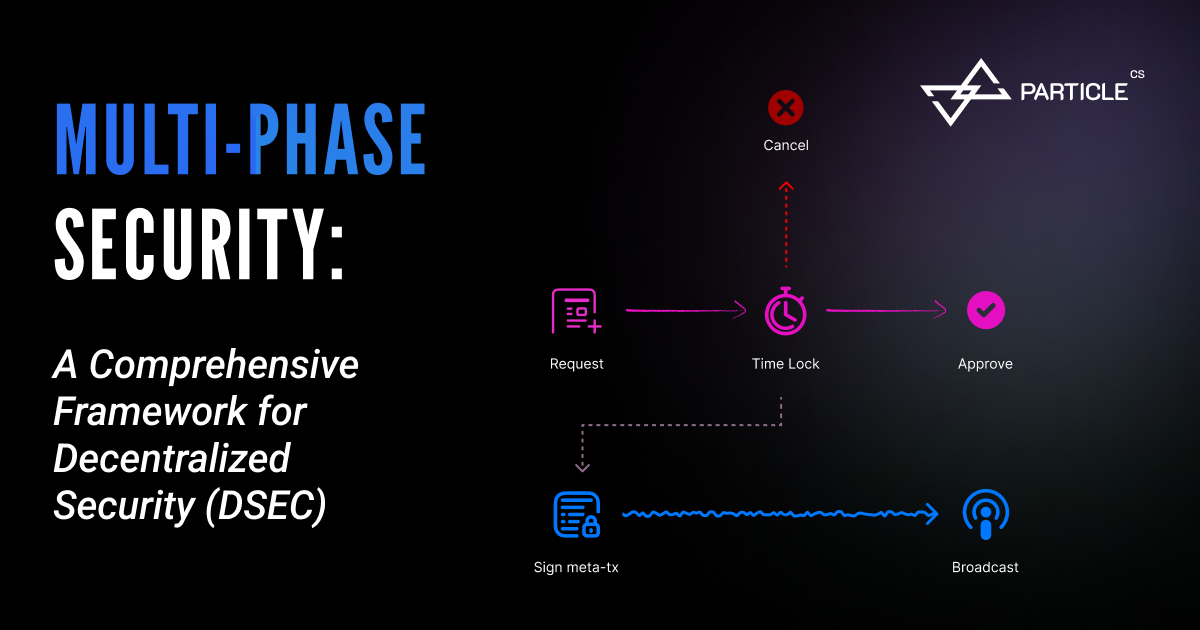
The Security Phases: How Multi-Phase Protection Works
The Multi-Phase Security Process follows a carefully designed sequence of phases that ensures maximum security while maintaining operational efficiency. Here’s how it works:
1. The Request Phase: Where Operations Begin
When initiating a blockchain operation:
- A new transaction request is created and signed
- The request is logged on-chain as a pending transaction
- No immediate execution is possible
- Only authorized roles can create requests based on their permissions
2. The Time Lock Phase: A Critical Security Layer
Every operation automatically enters a mandatory waiting period:
- The time lock begins immediately after request creation
- Duration is configurable based on:
- Operation type
- Asset value
- Risk level
- Regulatory requirements
- During this phase:
- The operation can be reviewed
- Suspicious activity can be detected
- The operation can be cancelled
- No execution is possible until the time lock expires
3. The Approval Phase: The Final Security Check
Once the time lock period expires:
- Only permitted roles can approve and finalize the transaction
- Custom security policies are enforced
- The operation can be:
- Approved for execution
- Cancelled if suspicious
- No modifications are allowed
- Once approved, the transaction becomes final and irreversible
4. Meta-Transaction Approval (Optional)
For operations using meta-transactions:
- Can be initiated while the time lock is in progress
- Enables separation of signing and broadcasting authorities
- Supports gas optimization through off-chain transaction preparation
- Allows role-based execution with distinct signing and broadcasting roles
- Provides additional flexibility for off-chain workflows
5. Broadcast Phase (Meta-Transaction Only)
For operations using meta-transactions from step 4:
- Final verification is performed before broadcast
- The signed operation is broadcast to the network
- Transaction becomes final and irreversible
- Complete audit trail is maintained
Key Security Features
Time-Based Controls
The system implements:
- Configurable time delays for different operation types
- Risk-based waiting periods
- Emergency cancellation windows
- Compliance-driven timeframes
- Automatic time lock enforcement
Role-Based Security
Security is enforced through:
- Granular permission sets
- Separation of duties
- Multi-party approvals
- Custom role definitions
- Role-specific time lock configurations
Recovery Mechanisms
The system provides robust recovery options:
- Emergency account ownership transfer for compromised accounts
- Role-based recovery with configurable recovery role
- Time-locked recovery procedures for secure transitions
- Comprehensive recovery audit trails
- Recovery policy enforcement through smart contracts
Implementation Through BloxChain Protocol and SandBlox
The Multi-Phase Security Process is powered by BloxChain Protocol, our Account Abstraction protocol. This implementation provides the core security framework, enabling smart contract-based security controls while maintaining blockchain’s trustless nature.
For developers and organizations looking to implement this security pattern, SandBlox offers ready-to-use security templates with an intuitive smart contract configuration UI. The platform makes it easy to deploy and manage multi-phase security workflows, bringing enterprise-grade security to blockchain operations.
Benefits for Different Stakeholders
For Organizations
Organizations implementing the Multi-Phase Security Framework gain eliminated single points of failure and recovery windows for suspicious activity. The system enables enterprise-grade security controls while maintaining decentralized principles. This approach provides flexible security policy implementation that can be tailored to specific organizational needs, whether for treasury management, DeFi operations, or institutional blockchain applications.
For Users
Users benefit from enhanced protection against key compromise and clear visibility into operation status. The framework maintains user control over assets while providing simplified security management. This combination of security and usability ensures that users can confidently manage their digital assets without compromising on protection or convenience.
For Developers
Developers can leverage a programmable security framework with customizable security policies. The system supports integration with existing systems and provides audit-ready implementation. This flexibility enables developers to build secure applications while maintaining control over the security architecture and implementation details.
Getting Started with Multi-Phase Security
Implementing Multi-Phase Security is straightforward:
- Explore the BloxChain Protocol to understand the technical foundation
- Discover security templates on SandBlox
- Contact our team for enterprise implementation support
Building Secure Blockchain Operations
The Multi-Phase Security Framework represents a significant advancement in blockchain security. By eliminating single points of failure and providing robust controls, it enables organizations to operate with confidence in the blockchain environment. Join the growing number of organizations that are implementing this security framework to protect their blockchain operations.
For updates on BloxChain Protocol developments, follow us on X.
Note: BloxChain Protocol is currently in testnet phase. Production deployments should be carefully evaluated based on your specific security requirements and risk tolerance.

